The financial landscape has undergone a dramatic transformation over the past decade. Blockchain technology now underpins transactions worth billions of dollars daily. However, this growth brings unprecedented security challenges. Organizations face sophisticated threats that can drain assets in seconds. Real-time blockchain threat monitoring has emerged as a critical business imperative. This analysis explores the tangible return on investment from implementing robust monitoring systems. We’ll examine how organizations are protecting their digital assets in 2026.
Understanding the Current Blockchain Threat Landscape
The blockchain ecosystem faces evolving security challenges every day. Cybercriminals have adapted their tactics to exploit vulnerabilities in decentralized systems. In 2025 alone, blockchain-related losses exceeded $2.1 billion according to industry reports. Smart contract exploits accounted for 43% of these incidents. Flash loan attacks and bridge vulnerabilities comprised another significant portion. Traditional security measures often fail in blockchain environments. Once a transaction executes, reversal becomes nearly impossible. Organizations need proactive defense mechanisms that detect threats instantly.
The Evolution of Blockchain Security Threats
Early blockchain attacks targeted individual wallets through phishing and social engineering. Modern threats have become far more sophisticated and automated. Attackers now deploy bots that monitor blockchain networks continuously. These systems identify vulnerable smart contracts within minutes of deployment. They execute exploits faster than human operators can respond.
Front-running attacks exploit the public nature of blockchain transaction pools. Malicious actors observe pending transactions and submit competing ones with higher fees. This manipulation yields guaranteed profits at legitimate users’ expense. Reentrancy attacks represent critical vulnerabilities in smart contract code. These exploits allow attackers to drain funds by recursively calling withdrawal functions. The infamous DAO hack demonstrated this vulnerability’s devastating potential. Cross-chain bridge attacks have proliferated as multi-chain ecosystems expand. These bridges transfer value between different blockchain networks. They present attractive targets with potentially massive payoffs for successful attackers.
The Business Case for Real-Time Monitoring
Organizations investing in blockchain infrastructure face a fundamental question. How do you protect assets in a decentralized, always-on environment? Real-time blockchain threat monitoring provides continuous surveillance of transaction patterns and network behavior. The financial impact of security failures extends beyond direct asset loss.
Quantifying the Cost of Security Incidents
A single successful attack can destroy years of business development. Direct financial losses represent only 30-40% of total impact. Legal fees and regulatory fines add another 20-25%. Operational disruption consumes 15-20% of resources. The most significant damage comes from reputation loss. Studies show 60% of users abandon platforms following major incidents. Share prices typically decline 15-30% after publicized failures. This market reaction reflects investor concerns about operational competence. Insurance premiums can increase by 200-400% after breaches. Some carriers refuse coverage altogether. This leaves organizations exposed without financial protection. The cascading effects create long-term business challenges.
ROI Calculations for Monitoring Solutions
Organizations typically spend $50,000 to $500,000 annually on monitoring infrastructure. This varies based on transaction volume and complexity. Enterprise-grade solutions serve major financial institutions. The average prevented loss from a single detected threat often exceeds annual costs. Organizations processing millions daily see even clearer benefits. The mathematics heavily favor preventive investment. Consider a DeFi platform handling $100 million in total value locked. A $200,000 annual monitoring system represents just 0.2% of protected assets. Preventing one major exploit justifies this investment many times over.
Cost-benefit analysis should include indirect savings. Reduced insurance premiums can offset 10-15% of costs. Improved compliance prevents potential fines worth millions. Customer retention improvements deliver substantial long-term value. Platforms with robust security reputations attract and retain more users. This translates to higher transaction volumes and increased revenue generation. The competitive advantage compounds over time.
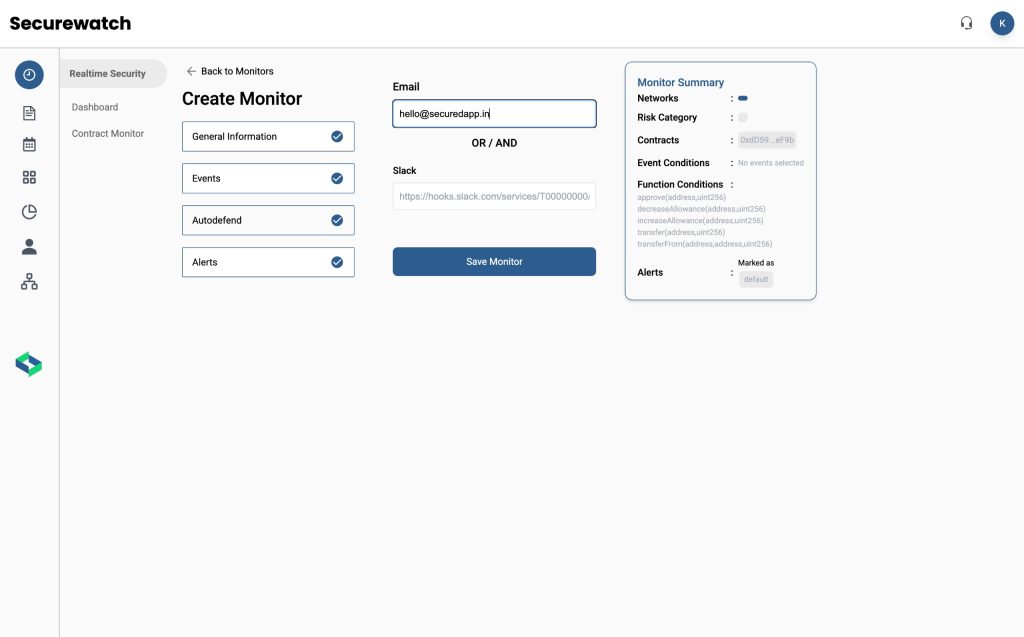
Core Components of Effective Real-Time Monitoring
Successful monitoring systems integrate multiple layers of detection and prevention. Organizations need comprehensive visibility across their entire blockchain infrastructure.
Transaction Pattern Analysis
Real-time transaction monitoring forms the foundation of threat detection. These systems analyze billions of transactions to identify suspicious patterns instantly. Anomaly detection algorithms establish baseline behavior for normal activity. They flag transactions that deviate from patterns. Machine learning models improve accuracy through continuous training.
Velocity checks identify unusually rapid sequences from single addresses. These patterns often indicate automated attack scripts or compromised accounts. Threshold alerts trigger when transaction volumes exceed normal parameters. Geographic analysis tracks transaction request origins. Sudden shifts in geographic patterns can indicate account takeovers. Transactions from high-risk jurisdictions receive enhanced scrutiny automatically.
Value-based filtering identifies significant asset movements requiring immediate review. Large transfers trigger review protocols. This prevents major losses while allowing normal operations to continue.
Smart Contract Vulnerability Scanning
Smart contracts execute automatically based on predetermined code logic. Flaws create opportunities for exploitation that attackers readily seize. Static analysis examines contract code before production deployment. It identifies common vulnerabilities like reentrancy bugs and integer overflows. This preventive approach stops problems before they cause damage.
Dynamic analysis monitors contract execution in real-time environments. It detects unexpected behavior that static analysis might miss. This includes interactions between multiple contracts creating emergent vulnerabilities. Formal verification mathematically proves contracts behave as intended. This rigorous approach eliminates entire classes of vulnerabilities. Continuous monitoring tracks all contract interactions. Unusual patterns trigger immediate alerts for rapid response.
Integration with Business Operations
Real-time blockchain threat monitoring must integrate seamlessly with existing operations. Organizations need solutions that balance security with operational efficiency. The best systems operate transparently without creating friction for legitimate users.
Automated Response Protocols
Speed determines success when responding to blockchain security threats. Manual intervention often arrives too late to prevent losses. Automated circuit breakers halt suspicious transactions before execution. These systems make split-second decisions based on predefined risk parameters. They prevent losses while minimizing false positives that disrupt legitimate activity.
Smart contract pause functions freeze operations during investigations. This capability proves essential when vulnerabilities are discovered in production systems. It prevents further exploitation while fixes are developed and deployed. Multi-signature requirements add protective layers to high-value transactions. Systems automatically enforce additional approval steps for transfers exceeding thresholds. This simple measure prevents unauthorized large-scale asset movements effectively.
Liquidity controls limit asset volumes exiting systems within specific timeframes. Attackers typically attempt to extract maximum value quickly. Rate limiting frustrates these attempts and buys time for intervention.
Compliance and Regulatory Reporting
Regulatory frameworks for blockchain continue evolving globally. Organizations must demonstrate robust security practices to satisfy requirements. Real-time monitoring systems generate comprehensive audit trails. These records prove essential during regulatory examinations. Automated reporting reduces compliance burden significantly.
Transaction monitoring for anti-money laundering integrates directly with blockchain systems. Suspicious activity reports generate automatically when patterns match criteria. This ensures regulatory obligations are met consistently. Know-your-customer requirements apply to most regulated blockchain businesses. Monitoring systems verify transactions comply with customer identification rules. They flag activities from unverified accounts for review before execution. mSanctions screening prevents transactions involving prohibited entities. Automated systems check parties against global sanctions lists in real-time. This protects organizations from inadvertent violations carrying severe penalties.
Technology Stack for Modern Monitoring Systems
Building effective real-time blockchain threat monitoring requires sophisticated infrastructure. Organizations must choose technologies that scale with growth. The monitoring stack spans multiple layers from blockchain nodes to user interfaces.
Node Infrastructure and Data Collection
Direct blockchain data access provides the fastest monitoring foundation. Organizations should operate full nodes for networks they use. Full nodes maintain complete blockchain history and current state. This eliminates third-party dependence and latency. Real-time monitoring requires millisecond-level response times that external services cannot guarantee.
Archive nodes enable deep historical analysis of transaction patterns. Historical data reveals trends and anomalies invisible in current-state-only systems. This long-term perspective proves valuable for identifying sophisticated attack campaigns. Light clients offer reduced requirements but sacrifice monitoring capabilities. They suit individual users but prove inadequate for organizational security. The tradeoff between cost and security tilts heavily toward full nodes. Multiple redundant nodes ensure monitoring continues during failures. Geographic distribution protects against regional outages. Load balancing distributes analysis tasks efficiently across available resources.
Analytics and Machine Learning Platforms
Raw blockchain data requires sophisticated analysis to extract security insights. Modern platforms leverage advanced analytics extensively. Stream processing frameworks analyze transactions in real-time. These systems handle thousands of transactions per second without delays. Apache Kafka and similar technologies form the backbone of high-throughput analysis.
Machine learning models identify complex patterns invisible to rule-based systems. Supervised learning trains on labeled examples of known attack types. Unsupervised learning discovers novel attack patterns without prior examples. Graph analysis reveals relationships between addresses and contracts despite obfuscation. Attackers often use multiple addresses to obscure activities. Graph algorithms uncover these connections effectively. Behavioral analysis establishes profiles for normal activity. Deviations trigger alerts regardless of specific attack signatures. This catches zero-day exploits that signature-based systems miss entirely.
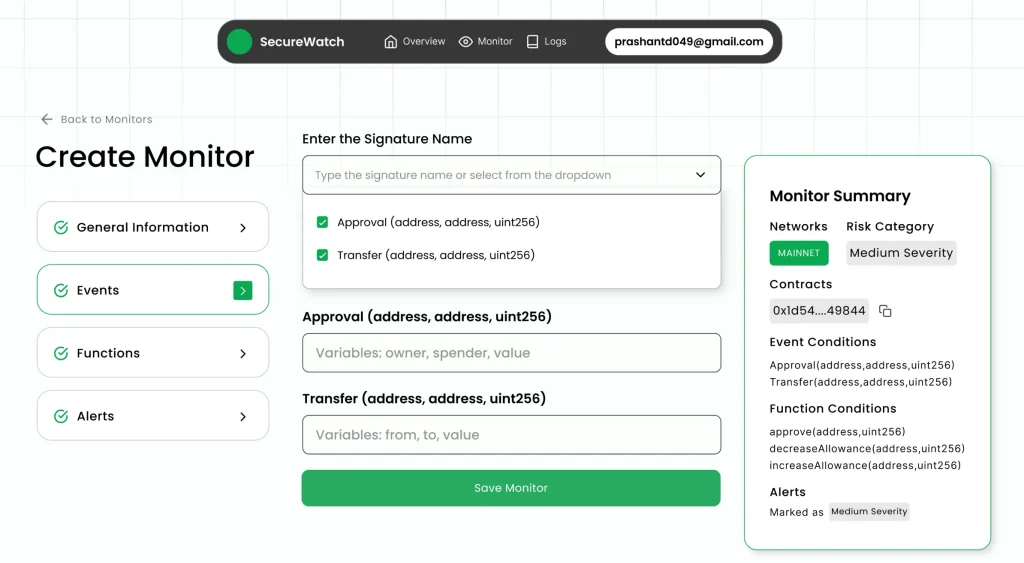
SecuredApp’s Approach to Blockchain Security Monitoring
Organizations need partners who understand blockchain technology and business requirements. Generic security solutions often miss blockchain-specific threats while generating excessive false positives. SecuredApp.io has developed specialized capabilities for real-time blockchain threat monitoring. Our platform combines deep blockchain expertise with proven security methodologies.
Comprehensive Visibility Across Blockchain Networks
Our monitoring infrastructure supports all major blockchain networks and protocols. Multi-chain support eliminates blind spots that attackers exploit. Cross-chain attacks represent growing threats as bridges proliferate between networks. Smart contract monitoring extends to complex DeFi protocols and custom implementations. We analyze interactions at multiple levels simultaneously. This reveals attack patterns that single-layer analysis misses completely.
Wallet monitoring tracks all addresses associated with your organization. This includes hot wallets, cold storage, and intermediate addresses. Comprehensive coverage ensures no assets escape protective monitoring. API integrations connect monitoring data with existing security systems. Organizations maintain preferred workflows while enhancing protection. Our platform enhances rather than replaces existing processes.
Customizable Alert and Response Systems
Different organizations face different risk profiles and operational requirements. Our platform adapts to your specific security needs rather than forcing generic configurations. Threshold-based alerts trigger when metrics exceed customizable parameters. Organizations define acceptable risk levels based on their own tolerance. The system enforces boundaries automatically without manual intervention.
Risk scoring assigns values to transactions based on multiple factors. High-risk activities receive immediate attention while low-risk ones proceed normally. This balanced approach maintains operational efficiency alongside security. Automated response playbooks execute predefined actions when threats are detected. Organizations configure these responses during initial setup. Automation ensures consistent, rapid responses regardless of time or staffing.
Manual review queues present ambiguous situations to human analysts. Machine learning handles clear-cut decisions while escalating edge cases. This hybrid approach optimizes both speed and accuracy. Integration APIs enable custom response mechanisms tailored to workflows. Organizations can trigger their own security tools automatically. This flexibility accommodates diverse operational environments effectively.
Measuring Business Impact and ROI
Implementing real-time blockchain threat monitoring represents significant investment. Organizations expect measurable returns that justify ongoing costs. Effective measurement requires tracking both prevented losses and operational improvements.
Key Performance Indicators for Monitoring Systems
Organizations should establish clear metrics before implementation. These KPIs demonstrate value to stakeholders and guide continuous improvement. Threat detection rate measures the percentage of actual attacks identified. High-performing systems detect 95% or more of real threats. This metric directly correlates with prevented financial losses. False positive rate indicates alerts involving legitimate activity. Excessive false positives waste analyst time and erode confidence. Best-in-class systems maintain false positive rates below 5%. Time to detection measures how quickly threats are identified after initiation. Faster detection prevents more damage before intervention occurs. Leading systems detect threats within seconds of suspicious activity.
Response time tracks intervals between detection and defensive action. Automated responses execute in milliseconds while manual processes take minutes. This metric highlights opportunities for further automation. Prevented loss value quantifies financial impact of stopped attacks. This represents the clearest demonstration of monitoring system value. Organizations should track both individual incidents and cumulative annual totals.
Long-Term Value Creation
Real-time monitoring delivers benefits that accumulate over time. Short-term ROI calculations often understate total value creation significantly. Reputation preservation represents substantial but difficult-to-quantify value. Organizations avoiding major incidents maintain customer trust. This translates to higher lifetime customer values and reduced acquisition costs. Regulatory compliance simplifies through automated monitoring and reporting capabilities. Organizations avoid fines while reducing compliance staff overhead. These combined savings often exceed monitoring system costs entirely.
Operational efficiency improves when security integrates smoothly with workflows. Employees spend less time on manual security tasks. This allows reallocation of resources to revenue-generating activities. Insurance premium reductions provide ongoing benefits year after year. Demonstrating robust security controls yields 15-25% savings. These reductions directly offset monitoring system costs. Competitive advantage emerges from superior security reputations. Organizations known for protecting customer assets attract more business. This premium positioning enables higher fees and better retention.
Implementation Best Practices
Successful deployment requires careful planning. Organizations should approach implementation systematically to maximize effectiveness. Rushed implementations often miss critical requirements or create operational disruptions.
Phased Deployment Strategy
Organizations should implement monitoring capabilities incrementally rather than all at once. This reduces risk while allowing learning from early phases. Initial deployment focuses on highest-value assets and critical systems. This protects the most important resources first while limiting scope. Success in phase one builds confidence for broader rollout.
Pilot programs test systems in controlled environments before production. Organizations identify configuration issues and refine alert parameters. This prevents disruptions to live operations during initial learning curves. Parallel operation runs new monitoring alongside existing measures initially. This validates detection capabilities without introducing new risks. Organizations can confidently transition when parallel testing proves effectiveness. Gradual expansion adds coverage for additional blockchains and wallets. Each expansion phase incorporates lessons learned from previous deployments. This iterative approach minimizes mistakes and optimizes configurations.
Staff Training and Change Management
Technology alone cannot deliver effective security without properly trained personnel. Organizations must invest in human capabilities alongside technical systems. Security analysts require training on blockchain-specific threat patterns. Traditional cybersecurity expertise doesn’t automatically transfer to blockchain environments. Specialized education programs fill knowledge gaps effectively.
Operations staff need clear procedures for responding to alerts. Documented playbooks ensure consistent responses regardless of who handles incidents. Regular drills maintain readiness and identify process improvements. Executive leadership should understand monitoring capabilities and limitations. This enables informed decision-making about risk acceptance and mitigation. Regular briefings keep leadership engaged with security programs. Development teams must integrate security considerations into workflows. Monitoring systems identify vulnerabilities that developers must address. Collaborative relationships between security and development prove essential.
Future Trends in Blockchain Security Monitoring
The blockchain security landscape continues evolving rapidly as technology advances. Organizations must anticipate future developments to maintain effective protection. Emerging trends will shape monitoring requirements over coming years.
Artificial Intelligence and Predictive Analytics
Current monitoring systems primarily react to detected threats. Next-generation platforms will predict and prevent attacks before they occur. Predictive models analyze historical attack data to forecast future patterns. These systems identify likely targets and attack vectors in advance. Organizations can implement protective measures proactively rather than reactively. Behavioral prediction anticipates how attackers respond to defensive measures. This enables strategic security planning that stays ahead of adversary tactics. The security arms race shifts in favor of defenders.
Automated threat hunting proactively searches for hidden compromises and vulnerabilities. Rather than waiting for alerts, systems actively seek signs of intrusion. This finds sophisticated attacks that passive monitoring might miss. Collective intelligence platforms share threat data across organizations. Attacks detected at one organization trigger protections for others. This collaborative approach benefits the entire ecosystem significantly.
Regulatory Technology Integration
Regulatory requirements will intensify in coming years. Monitoring systems must evolve to meet expanding compliance obligations. Real-time regulatory reporting will become standard rather than periodic submission. Regulators increasingly demand immediate visibility into organizational activities. Monitoring systems will automatically generate required reports continuously.
Privacy-preserving compliance techniques will balance transparency with confidentiality. Zero-knowledge proofs enable verification without disclosure. Organizations can prove compliance while protecting sensitive information. Cross-border coordination will create unified frameworks. Monitoring systems will need to satisfy multiple jurisdictions simultaneously. Flexible configuration will accommodate varying regional requirements effectively.
Conclusion: Strategic Imperative for 2026 and Beyond
Real-time blockchain threat monitoring has evolved from optional enhancement to absolute necessity. Organizations operating in blockchain environments cannot afford gaps in security coverage. The business case for comprehensive monitoring grows stronger each year. Direct ROI from prevented losses provides clear justification. Indirect benefits through reputation preservation and operational efficiency multiply total value. Implementation requires investment in technology, processes, and people. However, the cost of inadequate security far exceeds monitoring expenses. A single major incident can destroy organizations that cutting-edge monitoring would protect. SecuredApp.io stands ready to partner with organizations navigating blockchain security challenges. Our real-time blockchain threat monitoring solutions combine advanced technology with practical business understanding.



