The blockchain landscape has transformed from a niche technology into a fundamental infrastructure supporting billions of dollars in enterprise operations. Yet this transformation brings significant security challenges that traditional cybersecurity measures simply cannot address.
Last year alone, blockchain-related security incidents resulted in losses exceeding $2.3 billion across various protocols and platforms. These aren’t just numbers on a spreadsheet. They represent real businesses facing devastating financial consequences, damaged reputations, and lost customer trust. For enterprises operating in the blockchain space, whether managing cryptocurrency exchanges, developing decentralized applications, or integrating blockchain into supply chains, the question isn’t whether you need threat detection systems but rather how quickly you can implement them.

The challenge goes beyond conventional cybersecurity. Blockchain networks operate on fundamentally different principles than traditional systems. Transactions are irreversible, code execution is autonomous, and the attack surface spans smart contracts, consensus mechanisms, network protocols, and user wallets. A single vulnerability can cascade through interconnected protocols within seconds, draining funds before human operators even notice something has gone wrong.
Understanding the Blockchain Threat Landscape
Before diving into detection systems, you need to understand what you’re defending against. Blockchain threats have evolved considerably since the early days of simple wallet hacks and exchange breaches.
Smart contract vulnerabilities represent one of the most significant threat vectors. These self-executing programs manage billions of dollars in digital assets, yet they’re written by humans and therefore susceptible to coding errors, logic flaws, and unintended behaviors. The infamous DAO hack of 2016, which resulted in $60 million in losses, exploited a reentrancy vulnerability that allowed attackers to repeatedly withdraw funds before balance updates could occur. Similar patterns continue today, with flash loan attacks, oracle manipulation, and front-running attacks becoming increasingly sophisticated.
Decentralized finance protocols face unique challenges. The composability that makes DeFi powerful also creates complex interdependencies where a vulnerability in one protocol can affect dozens of others. When a price oracle gets manipulated, when a liquidity pool becomes imbalanced, or when governance mechanisms get exploited, the effects ripple through the entire ecosystem within blocks.
Network-level attacks target the consensus mechanisms and peer-to-peer infrastructure. Fifty-one percent attacks, eclipse attacks, and Sybil attacks threaten the fundamental integrity of blockchain networks. While these attacks require significant resources on major networks like Bitcoin or Ethereum, smaller chains and private enterprise blockchains remain vulnerable.
Then you have the human element. Social engineering, phishing attacks targeting private keys, and insider threats don’t exploit code vulnerabilities but rather human psychology and organizational weaknesses. These attacks often bypass even the most sophisticated technical defenses.
Why Real-Time Blockchain Threat Monitoring Matters
Traditional security approaches rely on periodic audits, manual reviews, and reactive incident response. This might work for systems where you can roll back transactions, freeze accounts, or restore from backups. Blockchain systems offer no such luxuries.
When an attack occurs on a blockchain network, you’re working against a fundamentally unforgiving timeline. Smart contract exploits can drain funds in a single transaction. Flash loan attacks execute, profit, and complete within the same block. Front-running bots monitor the mempool and can intercept profitable transactions before they even get confirmed. By the time your weekly security review identifies a problem, the damage has already occurred and cannot be reversed.
Real-time blockchain threat monitoring changes this dynamic entirely. Instead of discovering attacks after the fact, you detect anomalous patterns as they emerge, identify suspicious transactions before confirmation, and respond to threats while you still have options. The difference between real-time monitoring and periodic reviews is the difference between preventing a theft and filing a police report afterward.
Consider a practical scenario. Your enterprise operates a DeFi lending protocol. A sophisticated attacker identifies a vulnerability in your liquidation mechanism and begins preparing an attack. With real-time monitoring, you would notice unusual transaction patterns, detect the accumulation of positions that don’t match normal user behavior, and identify attempts to manipulate oracle prices. You could pause certain functions, alert your security team, and deploy countermeasures before the actual exploit occurs.
Without real-time monitoring, you would discover the attack only after millions in collateral have been liquidated incorrectly, users have lost funds, and your protocol’s reputation has been severely damaged. The technical post-mortem might be flawless, but the damage would already be irreversible.
Core Components of Effective Threat Detection Systems
Building an effective blockchain threat detection system requires multiple layers working in concert. No single technology or approach can address the full spectrum of threats you’ll encounter.
Transaction Monitoring and Analysis
At the foundation sits continuous transaction monitoring. Your system needs to observe every transaction touching your protocols, wallets, or smart contracts. This isn’t about storing complete blockchain data but rather filtering and analyzing relevant transactions in real time.
Effective transaction monitoring goes beyond simple pattern matching. You need behavioral analysis that understands what normal activity looks like for your specific use case. A large transaction might be perfectly normal for an institutional trader but highly suspicious coming from a newly created wallet. Multiple small transactions from different addresses converging on a single endpoint might indicate a coordinated attack or money laundering operation.
The monitoring layer should track not just individual transactions but also transaction graphs, following fund flows across multiple hops and identifying relationships between supposedly independent addresses. Sophisticated attackers use mixing services and complex routing to obscure their activities, so your detection systems need to see through these obfuscation techniques.
Smart Contract Security Monitoring
Your smart contracts need constant surveillance even after deployment. Runtime monitoring watches contract execution, tracking state changes, external calls, and gas consumption patterns. Unexpected behavior often manifests in these metrics before it becomes a full-blown exploit.
Access control monitoring ensures that privileged functions get called only by authorized addresses and that administrative keys haven’t been compromised. You should receive immediate alerts if ownership transfers occur, if emergency pause functions get triggered, or if unusual administrative actions take place.
For DeFi protocols specifically, you need specialized monitoring of liquidity pools, price oracles, and economic parameters. Sudden liquidity changes, price deviations from reference markets, or unusual arbitrage activities can all signal potential attacks or market manipulation.
Mempool Analysis
The mempool represents the collection of unconfirmed transactions waiting for inclusion in the next block. For threat detection, the mempool is invaluable because it shows you what’s about to happen before it actually occurs on the blockchain.
Sophisticated mempool monitoring can identify front-running attempts, detect pending large transactions that might impact your protocol, and spot patterns indicating coordinated attack preparation. If you see multiple transactions from different addresses all calling the same vulnerable function with carefully crafted parameters, you might be witnessing an attack rehearsal or the early stages of an exploit.
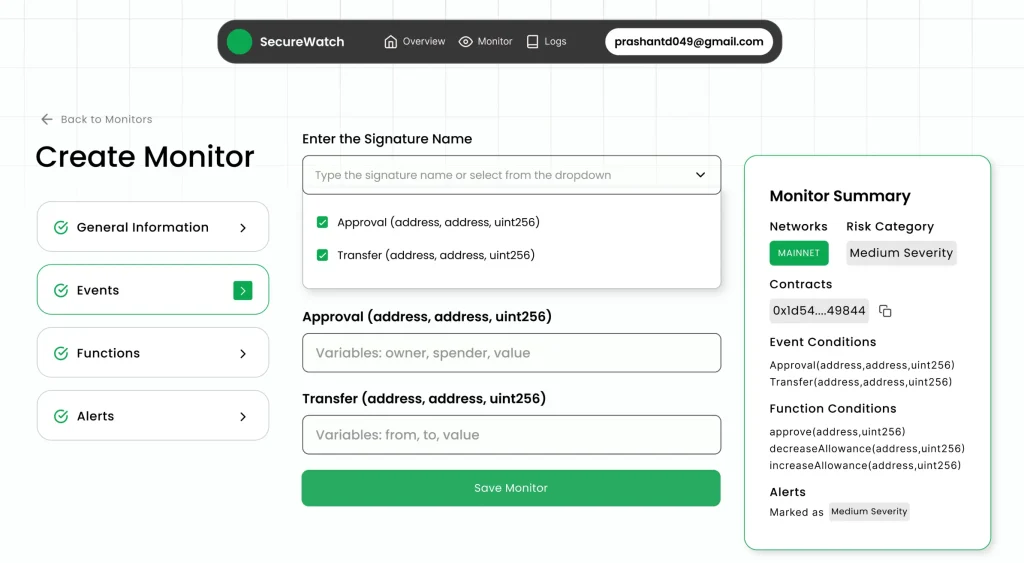
Solutions like SecureWatch from SecuredApp.io integrate mempool analysis into their comprehensive threat detection platforms, providing enterprises with those critical seconds or minutes of advance warning that can mean the difference between prevention and catastrophic loss.
Network-Level Security
Your detection system needs visibility into the peer-to-peer network layer. Unusual connection patterns, node isolation attempts, or abnormal consensus behavior can all indicate network-level attacks in progress.
For private or consortium blockchains, network monitoring becomes even more critical. You need to track which nodes are participating in consensus, identify any nodes exhibiting Byzantine behavior, and detect attempts to partition the network or overwhelm it with malicious peers.
Automated Alerting and Response
Detection without action is merely expensive observation. Your system needs intelligent alerting that routes different threat levels to appropriate responders. A critical smart contract exploit requires immediate escalation to your security team and potentially automatic defensive measures. Unusual but not immediately threatening activity might warrant investigation without triggering emergency protocols.
Alert fatigue is a real problem in security operations. Too many false positives and your team will start ignoring notifications. Your detection system needs sophisticated correlation and filtering to present actionable intelligence rather than raw data dumps.
Implementing Real-Time Blockchain Threat Monitoring
Understanding what you need is one thing. Actually implementing effective monitoring in your enterprise environment requires careful planning and execution.
Assessment and Planning
Start with a thorough assessment of your blockchain infrastructure and use cases. What chains are you operating on? What smart contracts have you deployed? Where are your critical assets? What would a successful attack look like against your specific implementation?
Different blockchain environments have different threat profiles. An enterprise running a private Hyperledger network faces different risks than one operating public Ethereum smart contracts. Your threat detection system needs to match your actual exposure.
Map out your current security posture honestly. Many enterprises discover during this assessment that they have significant blind spots. Maybe they’ve audited their smart contracts but have no runtime monitoring. Perhaps they track their own transactions but have no visibility into broader protocol interactions. Identifying these gaps is the first step toward addressing them.
Choosing the Right Tools and Partners
You face a build-versus-buy decision. Building custom threat detection infrastructure gives you complete control and customization but requires significant blockchain security expertise and ongoing maintenance. Most enterprises lack the specialized knowledge needed to build effective monitoring from scratch.
Partnering with established security platforms often makes more strategic sense. Platforms like SecureWatch from SecuredApp.io offer enterprise-grade blockchain security solutions that combine real-time threat monitoring, smart contract analysis, and incident response capabilities. These platforms benefit from intelligence gathered across many clients, identifying emerging threat patterns that any single organization might miss.
When evaluating solutions, look for comprehensive coverage across your technology stack, real-time processing capabilities rather than batch analysis, customizable alerting that matches your operational structure, and integration with your existing security infrastructure. The best blockchain threat detection systems don’t operate in isolation but rather complement your broader security program.
Integration and Testing
Deploying monitoring systems into production environments requires careful integration. You need to connect to blockchain nodes, ingest transaction data, and establish baseline behaviors without disrupting operations.
Start with observation mode before enabling automated responses. Let your system learn normal patterns and tune detection parameters. This learning period helps reduce false positives and ensures that when you do enable automated defenses, they trigger appropriately.
Testing is absolutely critical. Run attack simulations against test environments to verify that your detection systems actually identify the threats they’re designed to catch. Red team exercises where security professionals attempt to breach your defenses provide valuable validation of your monitoring effectiveness.
Operational Procedures
Technology alone doesn’t secure your blockchain infrastructure. You need clear operational procedures defining who responds to different alert types, what actions they’re authorized to take, and how quickly they need to act.
For critical alerts indicating active exploitation, you might need procedures for emergency contract pausing, transaction blocking, or network isolation. These procedures should be documented, practiced, and executable within minutes. When you’re facing a real attack, there’s no time to debate response protocols or hunt for access credentials.
Regular reviews and updates keep your monitoring relevant. Threat actors evolve their techniques constantly. Your detection systems need corresponding updates to maintain effectiveness. Schedule quarterly reviews of your monitoring rules, alert thresholds, and response procedures.
Advanced Considerations for Enterprise Deployments
Once you have basic monitoring established, several advanced considerations can further strengthen your security posture.
Multi-Chain Monitoring
Modern enterprises rarely operate on a single blockchain. You might have Ethereum smart contracts, private Hyperledger networks, and experiments with emerging chains like Solana or Polygon. Each chain has unique characteristics, different consensus mechanisms, and distinct threat patterns.
Unified multi-chain monitoring gives you centralized visibility across your entire blockchain footprint. This matters especially for cross-chain protocols where an attack on one chain could have implications for your operations on another. Comprehensive platforms provide this multi-chain visibility without requiring you to manage separate monitoring systems for each network.
Regulatory Compliance
Regulatory requirements around blockchain operations continue to evolve. Financial institutions face particularly stringent requirements around transaction monitoring, suspicious activity reporting, and audit trails.
Your threat detection system should support compliance needs through comprehensive logging, tamper-evident audit trails, and reporting capabilities. Being able to demonstrate to regulators that you have robust monitoring and can detect suspicious activities isn’t just good security practice, it’s increasingly a regulatory requirement.
Threat Intelligence Integration
Blockchain security benefits significantly from threat intelligence sharing. Known malicious addresses, emerging attack patterns, and vulnerability disclosures all provide valuable context for your monitoring systems.
Leading security platforms maintain threat intelligence feeds combining their own research with information from industry partners and blockchain security community. When a new attack pattern emerges, you want your systems updated with detection rules within hours, not waiting for your next security review cycle.
Machine Learning and Anomaly Detection
Static rule-based detection can only catch known attack patterns. Sophisticated attackers develop novel techniques specifically designed to evade conventional security measures.
Machine learning models excel at identifying anomalous behaviors that don’t match historical patterns, even when those behaviors don’t trigger specific rules. Training these models requires significant historical data and blockchain security expertise, which is why partnering with established security platforms that have already developed and validated these capabilities often makes more sense than building from scratch.
The Business Case for Investment
Implementing comprehensive blockchain threat detection systems requires investment. You’ll need budget for tools, personnel training, and ongoing operations. How do you justify this investment to stakeholders?
Start with the cost of potential incidents. Calculate what a successful attack would cost your organization. Consider direct financial losses, operational disruption, regulatory penalties, legal costs, and reputation damage. For most enterprises with significant blockchain exposure, even a single major incident would far exceed the cost of proper monitoring systems.
Look at insurance implications. Cybersecurity insurance providers increasingly consider blockchain security practices when underwriting policies. Demonstrating robust threat detection capabilities can result in better coverage terms and lower premiums.
Consider competitive advantage. As blockchain security incidents continue making headlines, customers and partners increasingly evaluate the security practices of the platforms they use. Being able to demonstrate enterprise-grade security monitoring becomes a differentiator in competitive markets.
Factor in operational efficiency. Effective monitoring reduces the time and resources spent on incident response and forensic investigations. Preventing attacks is invariably less expensive than responding to successful breaches.
Looking Forward
The blockchain threat landscape will continue evolving. Attackers will develop more sophisticated techniques. New vulnerability classes will emerge as smart contract complexity increases. Cross-chain interactions will create novel attack surfaces.
Your threat detection capabilities need to evolve accordingly. This isn’t a one-time implementation but rather an ongoing program requiring continuous improvement, regular updates, and sustained investment.
The enterprises that thrive in blockchain environments will be those that treat security as a fundamental operational requirement rather than an afterthought. Real-time blockchain threat monitoring represents the foundation of this security-first approach.
The technology exists today to detect and prevent the vast majority of blockchain attacks before they cause damage. The question isn’t whether effective threat detection is possible but whether your enterprise will implement it before or after experiencing a costly incident. Given the irreversible nature of blockchain transactions and the sophistication of modern attackers, waiting until after an incident to invest in proper monitoring is a risk few enterprises can afford.
Start by assessing your current blockchain security posture honestly. Identify your gaps. Evaluate solutions that can address those gaps comprehensively. Whether you build custom capabilities or partner with established platforms like SecureWatch, the important thing is taking action now rather than waiting for a security incident to force your hand.
The blockchain revolution promises tremendous opportunities for enterprises willing to embrace it. But those opportunities come with security responsibilities that traditional approaches simply cannot address. Real-time blockchain threat monitoring isn’t optional anymore. It’s the price of admission for serious enterprise blockchain operations.
FAQ Real Time Blockchain Threat Monitoring
Traditional security audits examine your smart contracts and blockchain infrastructure at a specific point in time, identifying vulnerabilities in the code itself. While valuable, audits provide a snapshot that becomes outdated the moment new threats emerge or your code interacts with other protocols. Real-time monitoring continuously observes actual blockchain activity as it happens, detecting suspicious transactions, unusual patterns, and active exploitation attempts. Think of audits as inspecting a building’s blueprints for structural flaws, while real-time monitoring is like having security cameras and motion sensors watching for intruders 24/7. You need both, but monitoring is what actually stops attacks in progress.
When a potential threat is detected, the response depends on the severity level and your configured protocols. For critical threats like active smart contract exploitation, the system can trigger immediate automated responses such as pausing vulnerable contract functions, blocking suspicious addresses, or alerting your security team through multiple channels. For medium-priority alerts like unusual transaction patterns, the system notifies your team for investigation while continuing to monitor the situation. Lower-priority anomalies get logged for review during regular security assessments. The key is having customizable response workflows that match your risk tolerance and operational requirements, ensuring you get protected without creating unnecessary disruptions to legitimate operations.
No security system can guarantee 100% protection against all attacks, and blockchain threat detection is no exception. However, comprehensive monitoring dramatically reduces your risk by catching the vast majority of attacks before they cause significant damage. The systems excel at detecting known attack patterns, suspicious transaction behaviors, and anomalous smart contract interactions. They struggle more with completely novel zero-day exploits that have never been seen before, though machine learning components can sometimes identify these through behavioral anomalies. The goal isn’t perfect protection but rather layered defense that makes successful attacks extremely difficult and ensures you detect and respond to threats as quickly as possible when they do occur.
Costs vary significantly based on your blockchain infrastructure complexity, transaction volume, and the level of coverage you need. For small to medium enterprises with limited smart contract deployments, commercial monitoring platforms typically start around $5,000 to $15,000 monthly. Larger enterprises with extensive multi-chain operations, high transaction volumes, and custom integration requirements might invest $50,000 to $100,000+ monthly. Building in-house solutions requires substantial upfront investment in specialized talent and infrastructure, often exceeding several hundred thousand dollars before you have functional monitoring. When evaluating costs, compare them against potential incident losses. A single major blockchain exploit can result in millions in losses, regulatory penalties, and reputation damage that far exceeds years of monitoring costs.



