The blockchain industry has grown tremendously over the past few years, but with this growth comes an increased risk of cyber threats and attacks. As we move through 2026, real-time blockchain threat monitoring has become not just important but absolutely essential for anyone involved in the blockchain ecosystem. Whether you are running a decentralised application (DApp), managing a cryptocurrency exchange, or simply holding digital assets, understanding how to monitor and respond to threats in real time can mean the difference between security and significant financial loss.
In this comprehensive guide, we will explore everything you need to know about real-time blockchain threat monitoring, from the basics to advanced implementation strategies that can protect your blockchain infrastructure.
Understanding Real-Time Blockchain Threat Monitoring
Real-time blockchain threat monitoring refers to the continuous surveillance and analysis of blockchain networks and transactions to identify, assess, and respond to potential security threats as they happen. Unlike traditional security measures that might detect issues after the fact, real-time monitoring provides immediate alerts and insights that allow you to take action before damage occurs.
The blockchain environment presents unique challenges for security monitoring. Transactions are permanent and irreversible, smart contracts operate autonomously, and the decentralised nature of these systems means that traditional centralised security approaches often fall short. This is where specialised real-time blockchain threat monitoring solutions come into play.
Modern monitoring systems track various activities across blockchain networks, including unusual transaction patterns, smart contract vulnerabilities, wallet behaviours, and network anomalies. They use advanced algorithms and machine learning to distinguish between normal operations and potential threats, providing actionable intelligence to security teams.
Why Real-Time Blockchain Threat Monitoring Matters in 2026
The blockchain threat landscape has evolved significantly. In 2026, attackers have become more sophisticated, using advanced techniques to exploit vulnerabilities in smart contracts, DeFi protocols, and blockchain infrastructure. Recent data shows that billions of dollars are still being lost annually to blockchain-related hacks and scams.
Real-time blockchain threat monitoring matters because it provides several critical advantages. First, it enables immediate threat detection, allowing you to respond to attacks within seconds rather than hours or days. Second, it helps prevent financial losses by identifying suspicious activities before they can cause significant damage. Third, it ensures compliance with regulatory requirements, which have become increasingly stringent as governments worldwide implement blockchain-specific regulations.
For businesses operating in the blockchain space, the reputational damage from a security breach can be devastating. Users trust platforms with their funds and personal information, and a single major security incident can destroy years of reputation building. Real-time monitoring helps maintain that trust by demonstrating a proactive commitment to security.
Additionally, the complexity of modern blockchain ecosystems makes manual monitoring practically impossible. With thousands of transactions occurring every minute across multiple chains, automated real-time blockchain threat monitoring systems are the only practical way to maintain comprehensive security oversight.
Common Blockchain Threats to Monitor
Understanding what you are monitoring for is crucial to effective threat detection. Several categories of threats require constant vigilance in the blockchain space.
Smart contract vulnerabilities remain one of the most significant risks. These include reentrancy attacks where malicious contracts repeatedly call functions before previous executions complete, integer overflow and underflow issues that can manipulate calculations, and access control problems that allow unauthorised users to execute privileged functions. Real-time blockchain threat monitoring tools can detect unusual contract behaviours that might indicate exploitation attempts.
Phishing and social engineering attacks have become increasingly sophisticated. Attackers create fake websites, impersonate legitimate projects, and use various psychological tactics to trick users into revealing private keys or approving malicious transactions. Monitoring systems can identify suspicious websites and warn users about potential scams.
51% attacks, where an entity gains control of the majority of a network’s mining power, remain a concern particularly for smaller blockchain networks. While less common on major networks like Bitcoin and Ethereum, these attacks can allow double-spending and transaction reversals. Monitoring network hash rates and mining pool distributions helps detect potential 51% attack scenarios.
Front-running and MEV (Maximum Extractable Value) attacks involve malicious actors observing pending transactions and placing their own transactions with higher fees to profit from advance knowledge. These attacks can cause significant losses, especially in DeFi trading. Real-time monitoring of mempool activities and transaction ordering can help identify and prevent such attacks.
Bridge exploits have become particularly concerning as cross-chain bridges facilitate asset transfers between different blockchains. Vulnerabilities in bridge smart contracts have led to some of the largest crypto heists in recent years. Continuous monitoring of bridge operations and smart contract states is essential for early threat detection.
Key Components of Real-Time Blockchain Threat Monitoring Systems
Effective real-time blockchain threat monitoring systems consist of several integrated components working together to provide comprehensive security coverage.
Transaction monitoring forms the foundation, involving continuous analysis of all transactions on relevant blockchain networks. This includes tracking transaction volumes, values, patterns, and relationships between addresses. Advanced systems use behavioural analysis to establish baselines for normal activity and flag deviations that might indicate malicious behaviour.
Smart contract monitoring focuses on the execution and state changes of deployed contracts. This involves tracking function calls, monitoring for unexpected state changes, analysing gas consumption patterns, and identifying potential vulnerability exploitations. Some systems even perform static and dynamic analysis of contract code to identify security issues before deployment.
Network monitoring examines the health and integrity of the blockchain network itself. This includes monitoring node activity, network consensus mechanisms, block propagation times, and potential signs of network attacks or disruptions. For proof-of-work chains, this might involve tracking hash rate distributions, while proof-of-stake chains require monitoring validator behaviours and staking patterns.
Wallet monitoring tracks the activities of specific addresses, particularly those belonging to your organisation or identified as high-risk. This includes monitoring for unauthorised access attempts, unusual withdrawal patterns, interactions with known malicious addresses, and compliance with expected behavioural patterns.
Threat intelligence integration connects your monitoring system with global threat databases and intelligence feeds. This allows the system to leverage collective knowledge about known attack patterns, malicious addresses, and emerging threats across the blockchain ecosystem.
Implementing Real-Time Blockchain Threat Monitoring
Implementing an effective monitoring system requires careful planning and execution. The first step involves assessing your specific needs based on your blockchain activities, risk tolerance, and regulatory requirements. A cryptocurrency exchange will have different monitoring needs compared to a DeFi protocol or an NFT marketplace.
Selecting the right tools and platforms is crucial. The market offers various solutions ranging from comprehensive enterprise platforms to specialised tools focusing on specific aspects of blockchain security. SecureDApp provides integrated solutions that combine multiple monitoring capabilities into unified platforms designed for the unique challenges of blockchain security.
Integration with existing systems ensures that blockchain threat monitoring works alongside your other security infrastructure. This might include connecting with incident response systems, SIEM (Security Information and Event Management) platforms, and communication tools to ensure alerts reach the right people at the right time.
Configuration and calibration require setting up appropriate thresholds and rules for alert generation. Too sensitive and you will be overwhelmed with false positives, too lenient and you might miss critical threats. This typically involves an initial learning period where the system establishes baselines for normal behaviour.
Team training ensures that security personnel understand how to interpret alerts, investigate potential threats, and respond appropriately. Even the best monitoring system is ineffective if alerts are ignored or misunderstood.
Best Practices for Effective Threat Monitoring
Following established best practices significantly improves the effectiveness of your real-time blockchain threat monitoring efforts.
Maintain comprehensive coverage across all blockchain networks and assets you interact with. Gaps in monitoring create blind spots that attackers can exploit. If your organisation operates across multiple chains, ensure monitoring extends to all of them.
Prioritise alerts based on severity and potential impact. Not all threats require immediate action, and effective prioritisation helps security teams focus their efforts where they matter most. Implement a clear classification system for different types of threats.
Establish clear response protocols for different types of threats. When an alert fires, everyone should know exactly what steps to take, who to notify, and what escalation procedures to follow. Document these procedures and practice them regularly through simulations.
Regularly update your monitoring rules and threat signatures as the threat landscape evolves. Attackers constantly develop new techniques, and your monitoring system must adapt to detect these emerging threats. Subscribe to threat intelligence feeds and participate in security communities to stay informed.
Conduct regular security audits and penetration testing to validate the effectiveness of your monitoring systems. Sometimes the best way to test your defences is to attempt to breach them in a controlled manner.
Maintain detailed logs and records of all monitoring activities and alerts. These logs are invaluable for forensic analysis after incidents, compliance reporting, and identifying long-term trends in threat activities.
Advanced Techniques in Real-Time Blockchain Threat Monitoring
As the blockchain security field matures, advanced techniques are emerging that significantly enhance monitoring capabilities.
Machine learning and artificial intelligence enable monitoring systems to detect subtle patterns and anomalies that might escape rule-based detection. These systems can learn normal behaviours for different types of users, contracts, and network activities, flagging deviations that might indicate threats. Behavioural analytics can identify zero-day attacks that have never been seen before by recognising suspicious patterns.
Graph analysis techniques map relationships between blockchain addresses, transactions, and contracts. This reveals hidden connections and can identify money laundering operations, criminal networks, and coordinated attack campaigns. Graph-based analysis is particularly effective at tracking the flow of stolen funds across multiple hops and mixing services.
Predictive analytics use historical data and trend analysis to anticipate potential future threats. By identifying patterns that typically precede attacks, these systems can provide early warnings before threats fully materialise, allowing proactive defensive measures.
Cross-chain correlation analysis examines activities across multiple blockchain networks to identify coordinated attacks or suspicious patterns that might not be apparent when looking at individual chains in isolation. As blockchain ecosystems become increasingly interconnected, this capability becomes more important.
Automated response systems can take immediate action when certain types of threats are detected, such as automatically pausing smart contracts when exploits are detected or freezing assets when unauthorised access is identified. While automated responses require careful implementation to avoid false positives causing disruption, they can significantly reduce response times for critical threats.
Regulatory Compliance and Threat Monitoring
The regulatory landscape for blockchain and cryptocurrency continues to evolve globally, and real-time blockchain threat monitoring plays a crucial role in compliance.
Anti-money laundering (AML) regulations require many blockchain businesses to monitor transactions for suspicious patterns that might indicate money laundering or terrorist financing. Real-time monitoring systems can flag transactions that meet regulatory thresholds or match known suspicious patterns, generating the necessary suspicious activity reports.
Know Your Customer (KYC) compliance involves verifying user identities and monitoring their activities for consistency with their risk profiles. Monitoring systems can alert when user behaviours deviate significantly from expected patterns, potentially indicating account takeover or fraudulent activities.
Data protection regulations like GDPR create obligations around protecting user data and privacy even in blockchain contexts. While blockchain’s transparency can create challenges for privacy, monitoring systems must be designed to comply with applicable privacy regulations while still providing effective security.
Regulatory reporting requirements often mandate detailed record-keeping and reporting of security incidents, suspicious transactions, and compliance metrics. Comprehensive monitoring systems with robust logging and reporting capabilities make regulatory compliance significantly easier.
Choosing a Real-Time Blockchain Threat Monitoring Solution
Selecting the right monitoring solution requires evaluating several factors based on your specific needs and circumstances. Coverage and compatibility ensure the solution monitors all blockchain networks you operate on and integrates with your existing infrastructure. Some solutions specialise in specific chains while others offer multi-chain support. Detection capabilities determine how effectively the solution identifies different types of threats. Evaluate the breadth of threat types covered, detection accuracy, and false positive rates. Request demonstrations with real-world scenarios relevant to your use case.
Scalability matters as your blockchain operations grow. Ensure the solution can handle increasing transaction volumes and expanding infrastructure without performance degradation. Usability and user experience affect how effectively your team can use the monitoring system. Intuitive dashboards, clear alert presentations, and efficient investigation workflows improve security outcomes. Support and documentation become critical when incidents occur. Evaluate the vendor’s support responsiveness, available documentation quality, and community resources.
SecureWatch: Advanced Real-Time Threat Detection for Blockchain
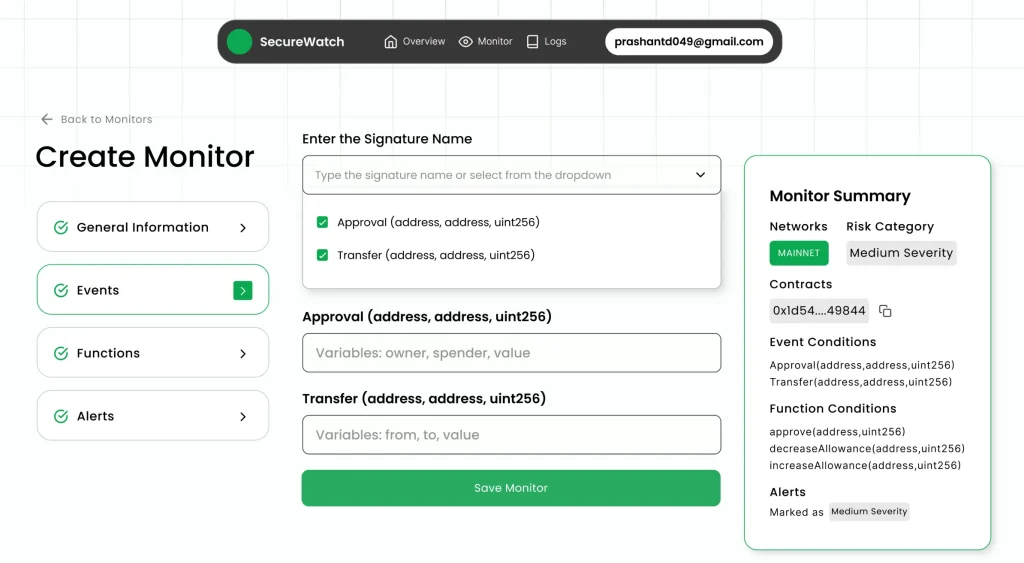
For organisations seeking a comprehensive real-time blockchain threat monitoring solution, SecureDApp’s SecureWatch provides enterprise-grade protection specifically designed for the unique challenges of blockchain security.
SecureWatch offers continuous monitoring across multiple blockchain networks, delivering instant alerts when suspicious activities are detected. The platform combines advanced machine learning algorithms with deep blockchain expertise to identify threats that traditional security tools might miss.
Key features of SecureWatch include real-time transaction monitoring that analyses patterns and behaviours to detect anomalies, smart contract surveillance that tracks contract executions and identifies potential exploits, wallet activity monitoring that alerts on unauthorised access attempts and unusual withdrawal patterns, and cross-chain threat correlation that identifies coordinated attacks across multiple blockchain networks.
The platform’s intuitive dashboard provides security teams with actionable insights, allowing them to quickly investigate and respond to threats. Automated alert prioritisation ensures that critical threats receive immediate attention, while customisable rules and thresholds allow organisations to tailor monitoring to their specific risk profiles.
SecureWatch integrates seamlessly with existing security infrastructure, supporting connections to SIEM systems, incident response platforms, and communication tools. This ensures that blockchain threat monitoring becomes part of your overall security strategy rather than operating in isolation.
What sets SecureWatch apart is its focus on blockchain-specific threats. While general security tools struggle with the unique characteristics of decentralised systems, SecureWatch was built from the ground up to understand blockchain transactions, smart contract logic, and the specific attack vectors that target blockchain infrastructure.
For businesses operating DApps, managing cryptocurrency exchanges, or working with DeFi protocols, SecureWatch provides the comprehensive protection needed to operate securely in today’s threat landscape. The platform’s proven track record of detecting and preventing real-world attacks makes it a trusted choice for organisations serious about blockchain security.
The Future of Real-Time Blockchain Threat Monitoring
The field of real-time blockchain threat monitoring continues to evolve rapidly as both threats and defensive technologies advance.
Artificial intelligence integration will become even more sophisticated, with systems capable of understanding context, predicting attacker behaviours, and autonomously responding to complex threat scenarios. We can expect AI models specifically trained on blockchain attack patterns to become standard.
Decentralised monitoring networks may emerge, where multiple parties contribute to collective threat intelligence while maintaining privacy through cryptographic techniques. This could create more comprehensive threat detection by pooling knowledge across the ecosystem.
Quantum-resistant monitoring will become necessary as quantum computing advances potentially threaten current cryptographic foundations of blockchain security. Monitoring systems will need to detect quantum-based attacks and verify quantum-resistant signatures.
Integration with Web3 identity systems will enable more sophisticated user behaviour analysis while respecting privacy through zero-knowledge proofs and decentralised identity frameworks.
Regulatory technology (RegTech) integration will streamline compliance monitoring as regulations become more specific and stringent. Automated compliance verification and reporting will become standard features of monitoring platforms.
Conclusion
Real-time blockchain threat monitoring has become an indispensable component of blockchain security in 2026. As the blockchain ecosystem continues to grow and attract both legitimate users and malicious actors, the ability to detect and respond to threats in real time can mean the difference between secure operations and catastrophic losses.
Implementing effective monitoring requires understanding the unique threat landscape of blockchain systems, selecting appropriate tools and technologies, following established best practices, and continuously adapting to evolving threats. While no security solution is perfect, comprehensive real-time blockchain threat monitoring significantly reduces risk and provides the visibility needed to maintain secure blockchain operations.
SecureDApp remains committed to providing cutting-edge real-time blockchain threat monitoring solutions that protect your blockchain infrastructure, assets, and users. By combining advanced technology with deep blockchain security expertise, we help organisations navigate the complex threat landscape with confidence.
FAQ
Real-time blockchain threat monitoring is the continuous process of observing blockchain networks, transactions, and smart contracts to identify security threats as they occur. Unlike periodic security checks, real-time monitoring provides instant alerts when suspicious activities are detected, allowing immediate response to prevent or minimise damage. The system analyses various data points including transaction patterns, smart contract executions, wallet behaviours, and network activities to distinguish normal operations from potential threats.
While traditional cybersecurity monitors centralised systems and servers, real-time blockchain threat monitoring must account for the decentralised, immutable, and transparent nature of blockchain networks. Blockchain monitoring requires analysing on-chain data visible to everyone, understanding smart contract logic, tracking cross-chain activities, and dealing with the irreversible nature of blockchain transactions. Traditional monitoring focuses on preventing unauthorised access, while blockchain monitoring also emphasises detecting exploitation of legitimate but vulnerable code and preventing irreversible financial losses.
Absolutely. While enterprise solutions offer comprehensive features, scaled-down monitoring tools and services are available for smaller operations and individuals. Even basic monitoring can alert users to unauthorised wallet access, suspicious transactions involving their addresses, or interactions with known scam contracts. Many wallet applications now include built-in monitoring features, and third-party services offer affordable monitoring for small businesses. The key is selecting monitoring appropriate to your risk level and technical capabilities.
Costs vary widely based on the scope of monitoring, number of blockchain networks covered, transaction volumes, and feature sophistication. Enterprise-grade solutions might range from several thousand to hundreds of thousands of dollars annually, while individual users might access basic monitoring for free or a few hundred dollars yearly. Cloud-based monitoring services typically charge based on transaction volumes or addresses monitored. When evaluating costs, consider that the expense of monitoring is typically far less than potential losses from undetected threats.
Advanced real-time blockchain threat monitoring systems can detect threats within seconds of occurrence. Transaction monitoring typically identifies suspicious patterns immediately as transactions are broadcast, often before they are confirmed on the blockchain. Smart contract monitoring can detect exploits within milliseconds of execution. However, detection speed also depends on the complexity of the threat, monitoring system configuration, and network conditions. Some sophisticated attacks designed to evade detection might take longer to identify even with real-time systems.
No security solution can guarantee complete protection, and real-time blockchain threat monitoring is no exception. However, it significantly reduces risk by providing early warning systems and rapid threat detection. The effectiveness depends on proper implementation, regular updates, skilled personnel interpreting alerts, and integration with comprehensive security strategies including secure development practices, regular audits, user education, and incident response planning. Monitoring is one essential layer in a defence-in-depth security approach.
Advanced monitoring systems with predictive capabilities can sometimes identify conditions that make attacks more likely and enable preventive measures. For example, detecting unusual network patterns might provide warning of an impending 51% attack, or identifying a newly discovered smart contract vulnerability might prompt defensive actions before exploitation. However, prevention depends on acting on monitoring insights quickly. Some automated systems can take immediate defensive actions like pausing vulnerable contracts, but these require careful configuration to avoid disrupting legitimate operations.



